 Analyzing Spear Phishing Attacks
Analyzing Spear Phishing Attacks

 Phishing Attack Prevention How To Identify Avoid Phishing
Phishing Attack Prevention How To Identify Avoid Phishing
 Why Phishing Attacks Are So Effective
Why Phishing Attacks Are So Effective
 The Ultimate Guide To Phishing
The Ultimate Guide To Phishing
 Phishing Detection And Loss Computation Hybrid Model A
Phishing Detection And Loss Computation Hybrid Model A
 Global View On Phishing Detection Based On Filtering
Global View On Phishing Detection Based On Filtering
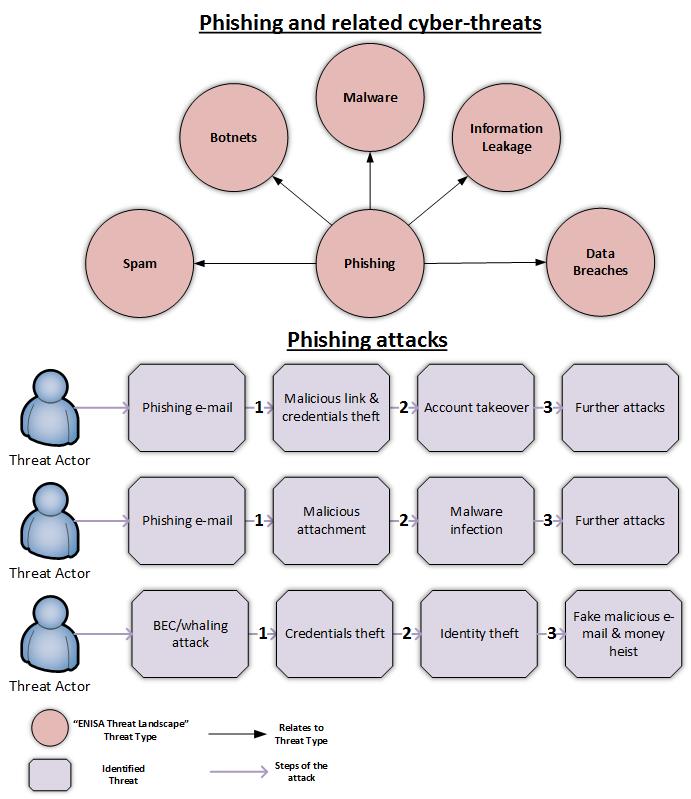 Phishing On The Rise Enisa
Phishing On The Rise Enisa
 What Is Vishing Voice Phishing Scams Explained How To
What Is Vishing Voice Phishing Scams Explained How To
 Can You Stop Phishing Emails Why What Youre Doing Now Is
Can You Stop Phishing Emails Why What Youre Doing Now Is
 Detecting And Characterizing Lateral Phishing At Scale The
Detecting And Characterizing Lateral Phishing At Scale The
Its The Deceiver And The Receiver Individual Differences
 Estimates Of The Number Of Social Engineering Based Cyber
Estimates Of The Number Of Social Engineering Based Cyber
 Something Else Is Phishy How To Detect Phishing Attempts On
Something Else Is Phishy How To Detect Phishing Attempts On
 Phishing Simulation Attack How To Avoid Phishing Attacks
Phishing Simulation Attack How To Avoid Phishing Attacks
 Evolution Of Phishing Attacks Phishingbox
Evolution Of Phishing Attacks Phishingbox
 5 Common Phishing Techniques Vade Secure
5 Common Phishing Techniques Vade Secure